CYBER SECURITY
Cyber security news updates in Kenya and Africa and tips on why it is critical for an enterprise to utilize cybersecurity best practices to avoid common cyber security threats.
-

A Sophisticated Malware Targeting Fintech and Online Trading Platforms Uncovered
Cybersecurity firm Kaspersky has discovered a new and highly sophisticated malware used in campaigns targeting fintech companies, and online trading…
Read More » -

Sophos Unveils Unified Partner Program to Accelerate Growth and Cybersecurity Delivery
Cybersecurity leader Sophos has launched a new global Unified Partner Program that brings together its partner ecosystem with that of…
Read More » -

Why Cybersecurity Is No Longer Optional in Africa’s Mobile‑First Economy
As Africa races ahead in its digital transformation, mobile devices have become the primary access point for banking, health services,…
Read More » -

Chinese-linked APT41 Group Behind Cyber Espionage Attack on Southern African Government Entity, Kaspersky
Kaspersky has revealed a sophisticated cyber espionage operation targeting a government IT department in Southern Africa. The attack has been…
Read More » -

iOS 26 Brings Subtle but Powerful Privacy Features That Could Change How You Use Your iPhone
Apple quietly dropped the public beta of iOS 26 this week, and while the flashiest features—like the new “Liquid Glass”…
Read More » -

Crypto Crime in 2025 Is Getting Personal as Hackers Move Beyond Exchanges and Go Global
From Silicon Valley to Seoul, crypto crime in 2025 is defying geography. Chainalysis’ mid-year update reveals that North Korea–linked hackers…
Read More » -

Sophos Named Leader in 2025 Gartner Magic Quadrant for Endpoint Protection for 16th Year
Sophos, a global leader in cybersecurity, today announced it has been named a Leader in the 2025 Gartner® Magic Quadrant™…
Read More » -

With Cyber Attacks Rising, Kenya’s New Insurance Rules Put Pressure on Insurers’ Boards
Kenya’s insurance industry is now under stricter cybersecurity oversight after the Insurance Regulatory Authority (IRA) introduced a sweeping framework that…
Read More » -

From OTP Bypass to Crypto Cash-Out: How the Kenyan Bank IT System Fraud Unfolded Without Detection
It reads like a cybercrime thriller — but for one unnamed Kenyan bank, it was a costly reality. In a…
Read More » -

Sophos Enhances Managed Risk with Internal Attack Surface Management
Sophos, a global leader of innovative security solutions for defeating cyberattacks, has announced the expansion of its Sophos Managed Risk…
Read More » -
How Israeli Intelligence Apps in Your Phone Quietly Took Over the App Stores
Some of the world’s most downloaded mobile apps—used for gaming, image editing, transit, and call screening—are quietly tied to one…
Read More » -

Median Ransom Now $1M, But 53% Paid Less Than Asked
Nearly 50% of companies in 2025 paid ransom to get their data back – the second highest rate of ransom…
Read More » -

Kenya ICT Sector Q3 2025: Starlink Rise, SIM Surge, Cyber Soars
Let’s be real—life in Kenya is digital now. Phones are everywhere. Money moves through mobile. Streaming is part of the…
Read More » -

Cybercrime in Africa Escalates as AI Scams, Phishing, and Deepfakes Undermine Digital Progress
As Africa races to embrace digital technology, a shadow is growing alongside it—cybercrime. From mobile banking fraud to deepfake scams,…
Read More » -

Sophos Empowers Partners with MDR Focus at Kenya Roadshow
Over 60 cybersecurity professionals convened in Mombasa last Friday for the Sophos Experience Partner Roadshow 2025, a major annual gathering…
Read More » -

Sophos Updates its Firewall Software
Cybersecurity firm Sophos has announced an update to its Firewall Software, now including Sophos NDR Essential, which is free for…
Read More » -

Kenya’s Digital Trust Crisis: How Criminals Are Weaponising WhatsApp to Defraud M-Pesa Users
Kenya is rightly celebrated as a global leader in mobile money innovation. But with innovation comes vulnerability, especially when the…
Read More » -

Check Point to Acquire Cybersecurity Firm Veriti
Check Point Software Technologies has revealed plans to acquire Veriti Cybersecurity, the first fully automated, multi-vendor pre-emptive threat exposure and…
Read More » -

Secure Banking; How to Avoid Losing Money in Fake Online Security Checks
While digital banking offers significant convenience, it also brings a growing challenge from sophisticated fraud. One of the latest scams…
Read More » -

Mart Networks Unveils Cybersecurity Offering for Fintechs
Mart Networks, a leading cybersecurity distributor in Africa and the Middle East, has announced the launch of a dedicated cybersecurity…
Read More » -

Sophos Boosts MSP Growth with New MSP Elevate Program
Sophos has launched MSP Elevate, a new business-accelerating program for managed service providers (MSPs). With the new program, the cybersecurity…
Read More » -

Gemini Nano Powers Chrome AI Scam Protection—What It Means for Your Online Safety
Chrome AI scam protection feature is now live and is perhaps the boldest initiative yet toward secure browsing. Google revealed…
Read More » -

Sophos Raises Data Theft Concerns Amid Surge of Chinese Cars in France
The recent success of the Shanghai Motor Show is a strong indicator of the growth of the Chinese automotive sector,…
Read More » -

Why Hacking Remains the Top Cybersecurity Threat
In the fast-growing digital world, our reliance on technology has become inescapable, with individuals communicating online via social media to…
Read More » -

The End of Passwords? World Password Day 2025 Explains the Shift to Passkeys
World Password Day 2025 is not simply an annual reminder; it is a notable milepost along the path of cybersecurity…
Read More » -

Microsoft Passwordless Future Explained: What Passkeys Mean for Your Digital Security
Effective May 2025, Microsoft has adopted passwordless login as the default for all new accounts, a decisive step toward making…
Read More » -

2024 Zero-Day Cybersecurity Report: What Google Didn’t Reveal About AI, N-Day, and Supply Chain Risks
While Google’s Threat Intelligence Group (GTIG) 2024 Zero-Day Cyber Security Report highlights valuable intelligence around zero-day exploits that have reached…
Read More » -

The Silent Surge: How Scam Call Centers Are Taking Root in Africa
For many decades, cybercrime in Africa-with the exception of some few ironic exceptions, was usually painted in a comic style…
Read More » -

Mart Networks Launches Invinsense 6.0 to Boost Cybersecurity in Africa
Mart Networks, a leading cybersecurity distributor in Africa and Middle East, today announced the launch of Invinsense 6.0, the latest…
Read More » -

Sophos Appoints Chris Bell to Lead Global Channel Strategy
Cybersecurity firm Sophos has named Chris Bell as Senior Vice President of Global Channel, Alliances and Corporate Development. In his…
Read More » -

Mart Networks, Infopercept Sign Cybersecurity Distribution Deal for Africa Region
Mart Networks Group, a leading value-added distributor, has announced a distribution partnership with Infopercept, a platform-led managed security services company…
Read More » -

Sophos Report: 56% of Cases Involved Attacks Using Existing Logins
Attackers primarily gained initial network access—56% of all MDR and IR cases—by exploiting external remote services like firewalls and VPNs…
Read More » -

Kenya Data Protection Crackdown: ODPC Is Fining Companies—But Is It Enough?
2024 saw the scatter-gun enforcement style of the Office of the Data Protection Commissioner (ODPC) in Kenya with 51 determinations…
Read More » -

UK Tech Firm Syntura Launches East Africa’s First AI and Cybersecurity Hub
Syntura, a UK-based technology company, has expanded to Africa with the launch of the Syntura Experience Center, the region’s first…
Read More » -

Cybersecurity Mistakes You Don’t Realize You’re Making (And How to Fix Them!)
In our digital world, even the most cautious users can fall victim to cyber-security traps without knowing it. Cybersecurity mistakes you…
Read More » -

The Illusion of Security: Why Senior Officials Using Signal Doesn’t Guarantee Safety
When media reports highlight the frequent usage of Signal for secure communication by senior government officials, people jump to the…
Read More » -

Foreign Cyber Threats in Kenya: National Strategies for Digital Defense
Cyber threats have become a national security challenge as Kenya is rapidly digitizing. Its digital assets, from financial institutions to…
Read More » -

Cybersecurity Discussions Take Center Stage at Safaricom Decode 3.0
Safaricom’s annual Engineering Summit (Safaricom Decode 3.0) kicked off on Wednesday with a strong emphasis on cybersecurity as an important…
Read More » -

MDR Users Report 97.5% Fewer Claims Than Endpoint-Only Users – Sophos Study
A new Sophos study has revealed the different impact that endpoint solutions, EDR/XDR technologies and MDR services have on claims…
Read More » -

Chester Wisniewski: Why the Supply Chain Remains a Prime Target for Cyberattackers
With the rise of digital transformation in recent years, businesses have become increasingly reliant on multiple partners and suppliers. This…
Read More » -

Kaspersky and Smart Africa Partner to Strengthen Cybersecurity in Africa
Kaspersky has signed a three-year Memorandum of Understanding (MoU) with Smart Africa to enhance cybersecurity across the continent. This partnership…
Read More » -

Infopercept Unveils Comprehensive MDR Solution
Infopercept, a global platform-led managed security services company has announced its new MDR solution called ‘Real MDR Solution.’ Delivered through…
Read More » -

Stalkerware Scandals: Data Leaks, Hacks, and Legal Crackdowns
A whole underworld exists for people who want to watch over and spy on their families. Several app creators sell…
Read More » -

Sophos and Pax8 Announce Partnership to Streamline Security Management
Cybersecurity firm Sophos has announced a strategic partnership with Pax8, the leading cloud commerce marketplace. Through this collaboration, Pax8’s network…
Read More » -

Over Half of Africans Fear Financial Losses From Cybercrime, Survey Finds
According to a recent survey conducted by KnowBe4 AFRICA, 58% of respondents are very concerned about cybercrime, a figure which…
Read More » -

Kenya Yet to Mandate Transition to Quantum-Resistant Cryptography, But Growing Awareness Sparks Conversations
Despite increasing global concern over the potential threats posed by quantum computing, Kenya has not yet passed legislation requiring government…
Read More » -

Kenya’s DCI X Account Hacked By Crypto Scammers
On Sunday evening, the X account of Kenya’s Directorate of Criminal Investigations (DCI) sent out posts inviting users to share…
Read More » -

Kaspersky reveals the evolution of ‘Nigerian’ email scams
Kaspersky researchers detected over 414,000 ‘Nigerian’ email scams. According to the cybersecurity firm, these emails relied on messages that lured…
Read More » -

Westcon-Comstor Extends Splunk Collaboration to EMEA
Westcon-Comstor, a global technology provider and specialist distributor, has announced that its Comstor arm has secured EMEA (Europe, Middle East and Africa)…
Read More » -

Malware Steals Crypto via Screenshots in App Stores
Kaspersky identified a new malware operation called SparkCat that has invaded the Apple App Store and Google Play Store. This…
Read More » -

Sophos Finalizes $859 Million Acquisition of Secureworks
Cybersecurity firm Sophos has announced the completion of its $859 million acquisition of rival Secureworks. With this acquisition, Sophos is now…
Read More » -

89% of IT leaders fear GenAI flaws threaten cybersecurity strategies, Sophos report
Despite 65% of IT leaders having adopted generative artificial intelligence (GenAI) capabilities, 89% of them are concerned that flaws in…
Read More » -

Sophos MDR Defends 26,000 Customers Worldwide
Cybersecurity firm Sophos today announced that its Sophos Managed Detection and Response [MDR] service has reached a major milestone, now protecting…
Read More » -

Antony Muchiri: Cyber Insurance – Why it matters and how to get it right
Cyber insurance has become a critical tool for companies aiming to protect themselves against the rising tide of cyberattacks. With…
Read More » -

Stay One Step Ahead of Fraud: Protect Your Finances This Festive Season
The festive season is here, bringing joy, celebrations, and increased financial activity. However, it also attracts heightened risks of fraud…
Read More » -

114 Cyber Attack Attempts Targeted Critical Government Systems
A total of 114 cyber-attacks on key critical information infrastructure were recorded by government agencies from January to August 2024.…
Read More » -

More than half of children in META region faced violent content on the Internet
Parents nowadays tend to have many concerns about the amount of time their children spend with their gadgets and what…
Read More » -

Sophos XDR Excels in MITRE ATT&CK® Evaluations: Enterprise
Cybersecurity firm Sophos today announced its strong results in the 2024 MITRE ATT&CK®Evaluations: Enterprise. Sophos XDR detected 100% of the adversary behaviors…
Read More » -

Abuse of Trusted Applications Grows by 51%, Sophos Report
Sophos, a global cybersecurity leader, has released “The Bite from Inside: The Sophos Active Adversary Report,” analyzing adversary behaviors and…
Read More » -

Google is Testing a Play Store Feature to Warn Users About Subpar Apps
Google is testing a new feature for the Play Store to ensure users download the best-quality apps and avoid low-quality…
Read More » -

African Telcos Increasingly Under DDoS Attacks for 2024, Report
While it’s true that every company is a potential target for distributed denial of service (DDoS) attacks, cybercriminals will often…
Read More » -

Password or No Password? Imagine a World Without it!
Passwords have been a bulwark of our digital security for decades, locking out unwanted intruders from emails, bank accounts, social…
Read More » -

Black Friday & Cyber Monday Security Tips To Keep Your Organization Safe
With Black Friday and Cyber Monday around the corner, we’re entering a high-risk period for cybersecurity. A recent Sophos report highlights that malicious…
Read More » -

South Africa Accounts for 22% of all Cyberattacks in Africa
South Africa accounts for 22% of cyberattacks on the continent and 25% of all dark web messages target organisations in…
Read More » -

SEACOM Partners With Cloudflare to Deliver Cybersecurity Solutions in Africa
SEACOM, a leading African connectivity and cloud services provider, together with Forefront, a cybersecurity managed services firm, have announced a…
Read More » -
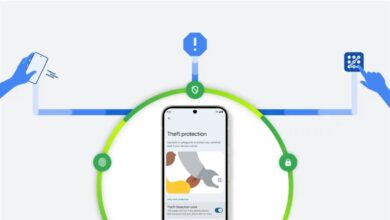
Google’s New Features to Combat Smartphone Theft in Africa
On one hand, phone theft has been a growing concern in many countries across Africa whereas on the flipside smartphone…
Read More » -

From QR Code to Compromise: The Growing Threat of “Quishing”
Cybersecurity firm Sophos today released the results of Sophos X-Ops research on a new type of threat, quishing. This new…
Read More » -

Sophos Unveils China-Based Threats in Pacific Cyber Defense
Sophos has today released “Pacific Rim,” a report detailing its defensive and counter-offensive operation over the last five years with…
Read More » -

Safaricom Urges For Investment in Advanced Cybersecurity Tech
In recognition of Cybersecurity Awareness Month, Kenya’s leading telco Safaricom is hosting a two-day industry-wide Cybersecurity Summit in Nairobi Kenya.…
Read More » -

IT, Education, Research Most Targeted Sectors By Cybercriminals
Information Technology, Education, and Research are the leading sectors most prone to cyber-attacks this year. This is according to the…
Read More » -

[Interview] Canon’s Quentyn Taylor on Cybersecurity and Current Vulnerabilities
October is Cybersecurity Awareness Month which aims to enhance global awareness about the importance of cybersecurity. Celebrated annually, this international…
Read More » -

Sophos Acquires Secureworks for $859 million
Cybersecurity firm Sophos announced on Monday that it has acquired Secureworks from Dell Technologies for $859 million in cash to…
Read More » -

How to Be Cautious When Downloading Google Play Store Apps
While Google attempts to remove harmful apps from its Play Store, some still manage to appear, access user information, and…
Read More » -

Sophos unveils new XGS desktop firewalls and software
Sophos has announced the launch of new XGS Series desktop firewall appliances and updated software aimed at enhancing automatic threat protection…
Read More » -

Two-Thirds of Healthcare Organizations Hit by Ransomware, Sophos
The rate of ransomware attacks against healthcare organizations has reached a four-year high since 2021. This is according to a…
Read More » -

NCBA Bank turns to new tech for enhanced cybersecurity
The Central Bank of Kenya’s 2023 Banking Sector Innovation Survey revealed that cyber-risk is the most significant challenge for financial…
Read More » -

Most educational organizations paid more than the initial ransom, Sophos Survey
The average ransom paid by educational institutions is $6.6 million for primary education institutions and $4.4 million for higher education…
Read More » -

Liquid expands cyber security offering for businesses in EA
Liquid Intelligence Technologies has announced the expansion of its Cybersecurity Fusion Center (CSFC) product line with an exciting new cybersecurity…
Read More » -

Operation Crimson Palace, Chinese State-sponsored espionage, expands in Southeast Asia, Sophos
A new by Sophos report has detailed the latest developments in a nearly two-year-long Chinese cyberespionage campaign in Southeast Asia.…
Read More » -

NCBA invested $31m in 2023 on cybersecurity
NCBA Bank has announced that it invested nearly $31 million in 2023 to strengthen and enhance its cybersecurity infrastructure. Speaking…
Read More » -

Sophos Launches Dedicated Customer Success Team
Cybersecurity firm Sophos has launched a customer success program for its customers and channel partners across different regions. The new…
Read More » -

Ransomware Groups weaponize stolen data to increase pressure on targets, report
Cybercriminals are weaponizing stolen data to increase pressure on targets who refuse to pay, a new report by cybersecurity firm…
Read More » -

Telecoms are prime targets for cyberattacks in 2024, Kaspersky report
Telecom, mass media, and construction development companies are the top cyberattack targets in the first half of 2024, according to…
Read More » -

Kaspersky Adds AI-Focused Module to its Security Platform
Kaspersky has announced the launch of a new AI-focused module within its Kaspersky Automated Security Awareness Platform (ASAP). Kaspersky says…
Read More » -

Energy and Water sector ransomware recovery costs hit $3M, Sophos survey
The median recovery costs for two critical infrastructure sectors, Energy and Water, quadrupled to $3 million over the past year,…
Read More » -

African countries among the most targeted by malware, report
Seven African countries have been ranked in the Top 20 most attacked by malware. This is according to the Global…
Read More » -

Ben Gelman: How Much Will AI Really Help Cyber Security?
The field of information security is undergoing a significant transformation with the development of artificial intelligence [AI] technologies. New AI…
Read More » -

76% of Companies Improved Their Cyber Defenses, Sophos Survey
97% of organisations with a cyber policy invested in improving their defenses to help with insurance, with 76% saying it…
Read More » -

Hacktivist group Anonymous sends warnings to Kenyan government to allow citizen protests
Kenyan businesses and institutions are on tenterhooks as global hacktivist group Anonymous sent warning salvos to the country’s government to…
Read More » -

Suspected Chinese hackers step up attacks on Kenyan government agencies
Kenyan government agencies were among the organisations targeted by suspected Chinese hackers. This is according to a new report released…
Read More » -

Chester Wisniewski: Ransomware Gangs and The Media: Between Control and Mistrust
Cybercriminals traditionally operate in the shadows of the Darknet and prefer to avoid the spotlight to ensure the success of…
Read More »