Sophos warns internet users against Petya Ransomware outbreak
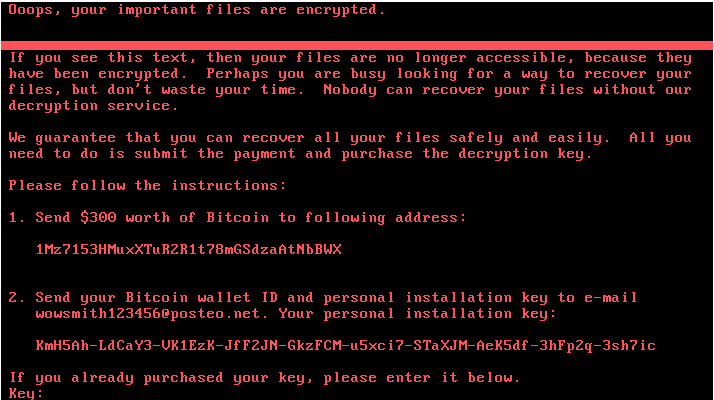
Many any organizations in Europe and the US were last week crippled by yet another ransomware attack known as “Petya”. This is the second major global ransomware attack after WannaCry in just two months.
Petya is a new variant of the Petya ransomware family and was first discovered in 2016. It encrypts MFT (Master File Tree) tables and overwrites the MBR (Master Boot Record), dropping a ransom note and leaving victims unable to boot their computer. This new variant is particularly virulent because it uses multiple techniques to spread automatically within a company’s network once the first computer is infected.
The Peyta cyberattack has now struck computers in at least 65 countries and is spreading at an alarming speed in other countries. Peyta is spreading using a vulnerability in Microsoft Windows that the software giant patched in March 2017.
Unlike WannaCry,Petya attempts to spread internally by breaking admin passwords and infecting other PCs on the network using remote admin tools. It can also spread internally by infecting network shares on other computers.
Read>>Infographic: Understanding the WannaCry Ransomware
According to an article pubished on TechCrunch, analysts think Petya ‘ransomware’ was built for targeted destruction, not profit. ‘’The malicious software’s code and other evidence indicate that the profit motive may have been a camouflage for an act of cyber-espionage targeting Ukraine.’’ the article said.
Ransomware is one of the most widespread and damaging threats that internet users face. Since the infamous CryptoLocker first appeared in 2013, “We’ve seen a new era of file-encrypting ransomware variants delivered through spam messages and Exploit Kits, extorting money from home users and businesses alike”, says Harish Chib, Vice president Middle East and Africa, Sophos
According to Chib, Sophos Endpoint Protection products are protected against this new ransomware variant so their customers have nothing to worry about. He notes that Sophos Intercept X customers were proactively protected with no data encrypted, from the moment this new ransomware variant appeared.
To avoid such attacks, Sophos is urging users to ensure systems have the latest patches, including the one in Microsoft MS17-010 bulletin. Users should also consider blocking the Microsoft PsExec tool from running on users’ computers using Sophos Endpoint Protection. They should also back up regularly and keep a recent backup copy off-site and also void opening attachments in emails from recipients you don’t know.


