
JuicyScore, a global leader in anti-fraud and risk management solutions entered the Kenyan market recently.
The firm offers anti-fraud and risk management solutions to digital lenders, insurance companies, e-commerce, and classifieds and create technologies for fraud prevention in online business and financial products risk reduction.
Headquartered in Singapore and Dubai, JuicyScore provides cutting-edge solutions to 80+ clients across 25+ countries. The core competitive advantage is that the company does not utilize personal or sensitive data and direct consumer identifiers.
In this interview, Mikhail Marchenko, the Co-Founder talks to TechTrends Media about the company’s products and how local organizations can take advantage of them.
What is your prediction for the year and how can Fintechs cushion themselves from risk-related issues in 2023?
The consumption of digital credit will significantly increase this year. This can be attributed to increased financial inclusion, smartphone penetration, and easy access to credit. However, we are aware of the fact that fintech in Kenya will face a lot of challenges, but those players who will pay more attention to implementing modern and cost-effective fraud prevention technologies, that provide economic payback for your business, will turn them to opportunities to grow and be head and shoulders above the competitors.
With the penetration of new vendors to Kenya, which do not use any personal data of a customer, online businesses can mitigate operational risks really well, using advanced technological credit scoring solutions, based on digital footprint of the device (mobile phone in particular) and add more value to the data no one of their competitors even thought to use and increase the acceptance rate significantly as well as to exclude reputational losses related to severe data breaches and help the customer to start creating it’s credit history. At the same time, they obtain a rather heavy competitive advantage and are now able to create more tailored solutions, based on customer needs and user experience.
What kind of solutions does JuicyScore offer to mitigate the predicted risks?
Our product *JuicyScore* helps online businesses to identify high-risk applications and take effective anti-fraud measures. We have developed the most stable probabilistic Device ID with low false positives, which is independent of device manufacturer and comply with all privacy policies. The wide technological stack also includes randomization, anonymization, and virtualization detection as well as the detection of remote control. This product also provides online businesses with AI-based credit scoring – using “alternative data” you can detect reliable, predictive patterns. On average JuicyScore clients get 10+ ROI. Our API is unified for both web and mobile channels. The solution is fully compliant with current and prospective regulating rules, browsers’ and operational systems’ security policies.
Apart from that, continuing the trend of non-personal data as a part of loan pipeline for neobanks and alternative lending, we offer the *JuicyID* product, which allows companies to strengthen the external perimeter of the client’s personal account on the web portal or mobile application of a financial institution, identify a large set of dangerous device anomalies, highlight related devices of the same user, and, as a result, reduce losses. In addition, JuicyID can be effectively used as part of the protection of the personal account of creditors – the JuicyID data vector allows to build rules and models to protect financial and quasi-financial information, flexibly configure access authorization rules depending on the risk level of the device or user.
Why is it important for Fintechs to invest in such solutions in the era of cyber-attacks and fraudsters?
Fintechs have identified fraud as an element of credit risk and has a very big impact on the customer journey and the reputation of the organization. It is therefore very important for the Fintechs to protect their customers by verifying and authenticating using data and technology that will be able to tie the device to the offline persona.
To mitigate this, we have a distinguished feature that uses a wide stack of technologies, designed to speed up the interaction with a client, making payments, and conducting other financial transactions. At the same time, due to the pandemic a large number of users switched to the online channel as a main source of obtaining financial services. In fact, online channels allow companies to reduce operating costs significantly, as well as to gain access to a wider audience on the one hand, and not to risk one’s health speaking about the clients on the other hand.
However, today we are witnessing a really big leakage of personal data day by day and when it comes to the Internet it leads to an increasing number of cyber-attacks globally. That is why the secure storage of user data is becoming one of the most important issues in today’s online business. So, as a way to compete successfully with traditional financial institutions, it is necessary to take into account the importance of privacy and data protection, which is growing immensely.
Now that Artificial Intelligence has become an integral part of risk monitoring architecture, do JuicyScore Solutions adopt such technologies for efficiency and quick detection of risk or fraud on Fintech’s infrastructure?
Actually, JuicyScore is based on AI/ML technologies, to be precise we have a wide stack of technologies of device and virtual user authentication, matching technology between virtual users and their devices, and a patented model of fraud risk prevention. Machine learning methods are also powerful tool that allows, with an understanding of the nature of the data and the correct application of modeling methods, to achieve practical solutions, such as predicting various kinds of risks.
What are some of the things that fintechs overlook when deploying risk management solutions or fraud detectors in a system?
One of the most important things risk officers should pay more attention to in terms of dealing with risk management and fraud prevention is the wider use of alternative user data in the decision-making system, which, on the one hand, in many cases have sufficient information value, and on the other hand, if such data is lost or compromised, data breach in any way will not cause serious damage: fraudsters simply cannot use such data to obtain significant benefits.
Alternative data refers to data obtained from non-traditional sources. For example, signs of digital fingerprint falsification, markers of shady user behavior, which indicate a high risk of the applicant, etc.
Authentication process- The process of determining whether someone or something is, in fact, who or what it says it is. Matching the credentials in a device with the user of the device who is an offline persona.
Use of both data and technology to detect fraud and credit risk-Most institutions use data from the KYC process and other third-party sources and overlook the technology (Machine learning/Artificial intelligence)
Why is it important for management of fintechs to frequent audits on their systems when dealing with financial systems that risk management solutions?
A herd of buffaloes runs with the speed of the slowest bison. If there are any flaws in your decision-making system in terms of risk management and fraud protection, be sure that fraudsters’ reaction won’t keep you waiting too long. We believe that it’s much easier to prevent fraud rather than to deal with its consequences, which occurred due to an ill-timed audit. It’s always better to understand – if you don’t walk today, you will have to run tomorrow. Implementing new modern technologies and solutions with proven efficiency, you may protect your business easily.
In comparison with other markets for fintechs, is Africa more at risk and why?
In the last few years, we have spotted some trends, for example, a big surge of randomizers used by fraudsters, for example, the number of randomizers has increased from 0,1% to 3,5% and Africa is no exception.
We are going to share our new methodology benefits, which allow online businesses to identify high-risk and carry out segmentation throughout the entire flow of applications. We are also proud to announce the launch of our new product: automatic risk management reporting, which will be available to all our clients in Q1 2023.
The aggregated results show a comparison of fintech companies in different regions of the world, data are given as of November of 2022
Our methodology is based on the division of the entire session space into 4 groups, which are the following:

The key positive factor of this approach is that all the high-risk sessions inevitably fall into one of the four groups, therefore, we can spot 100% of all possible online fraud attempts.
Another advantage is that this approach does not depend on the country, technologies, local legislation, etc., which means that one can compare various online resources and countries.
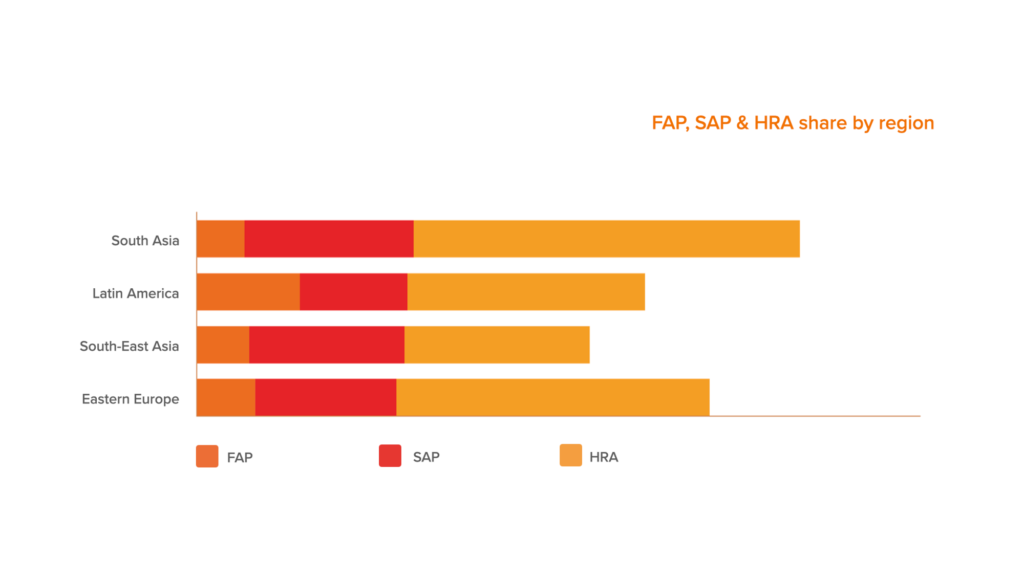
Here you can see the share of FAP, SAP & HRA, which sums up the level of toxic/high-risk sessions by region.
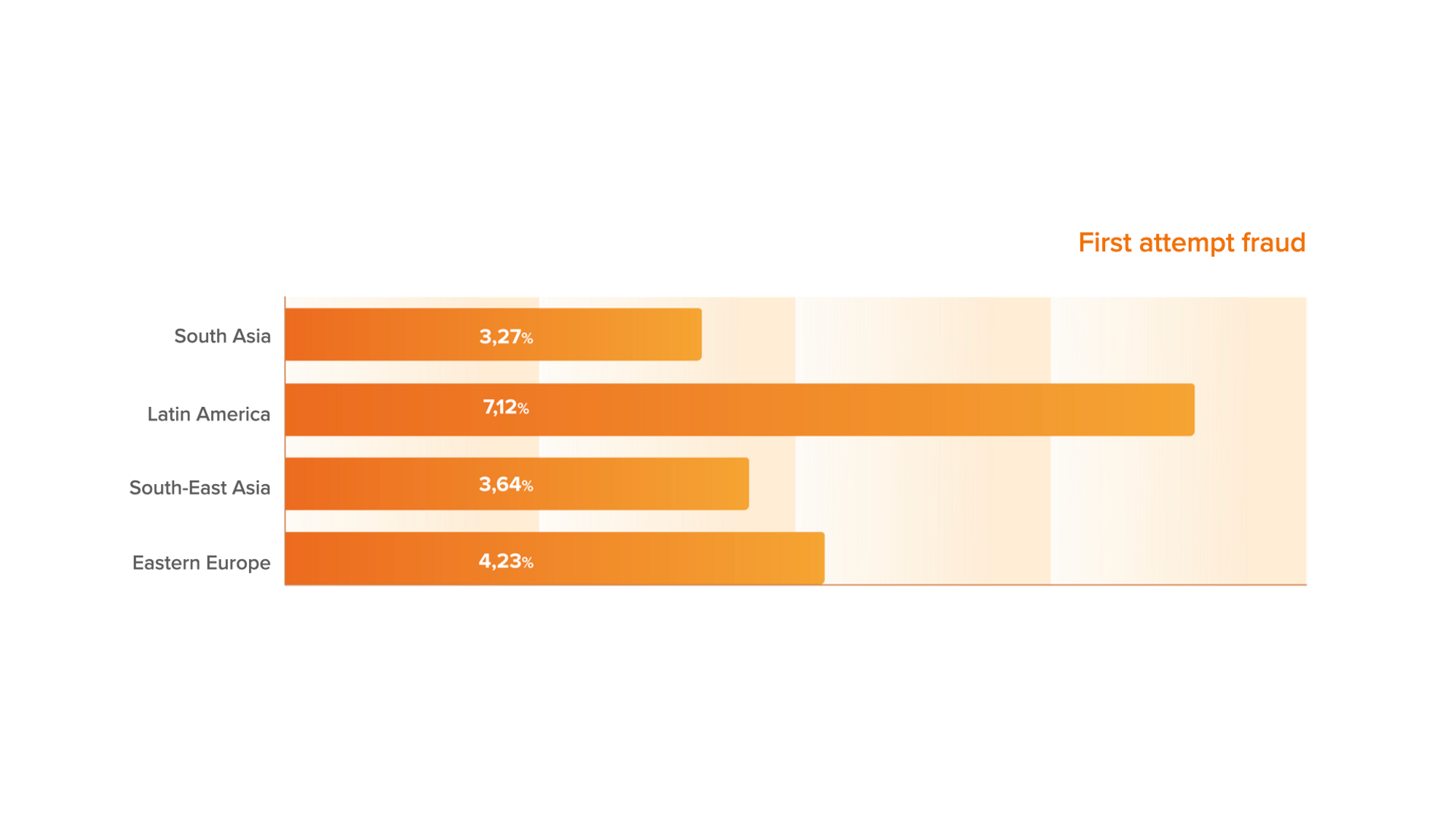
In the First attempt fraud category we included a combination of 50+ rare events with a high probability of fraud related to a device technical manipulation, in particular, the use of randomizers, Some browser, or operating system anomalies. We also noticed that the number of First attempt fraud in Latin America exceeded the same indicator in other regions almost two times, which may be an illustration of the increase of single fraudsters attacks in this region over the past month.
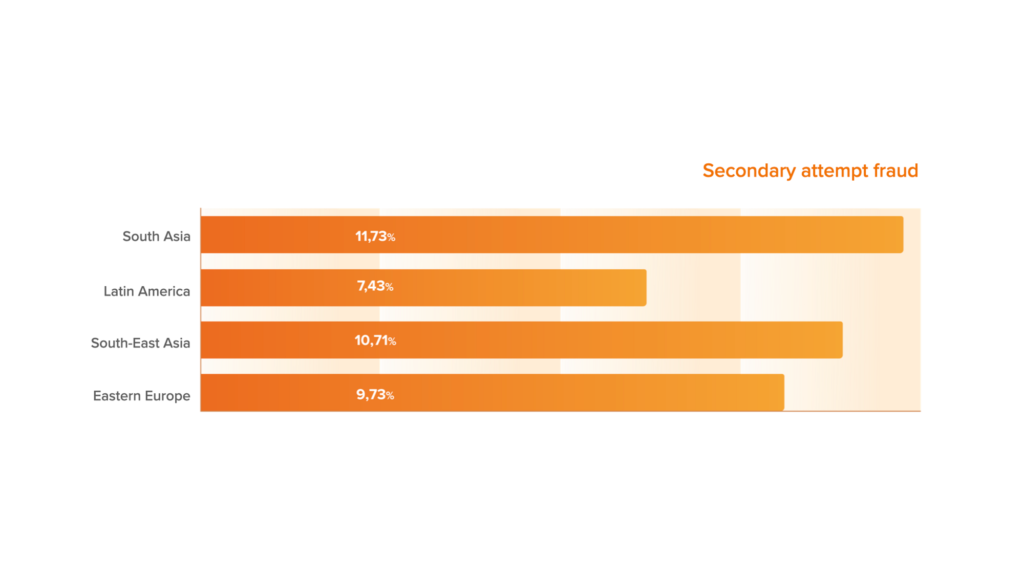
In the Secondary attempt fraud metric, we included repeated devices as well as repeated users. We also noticed that the number of Second attempt fraud in South and South-East Asia and in Eastern Europe remains at a relatively high level, which indicates that fraudsters have been using large amount of data from the fraud net recently.
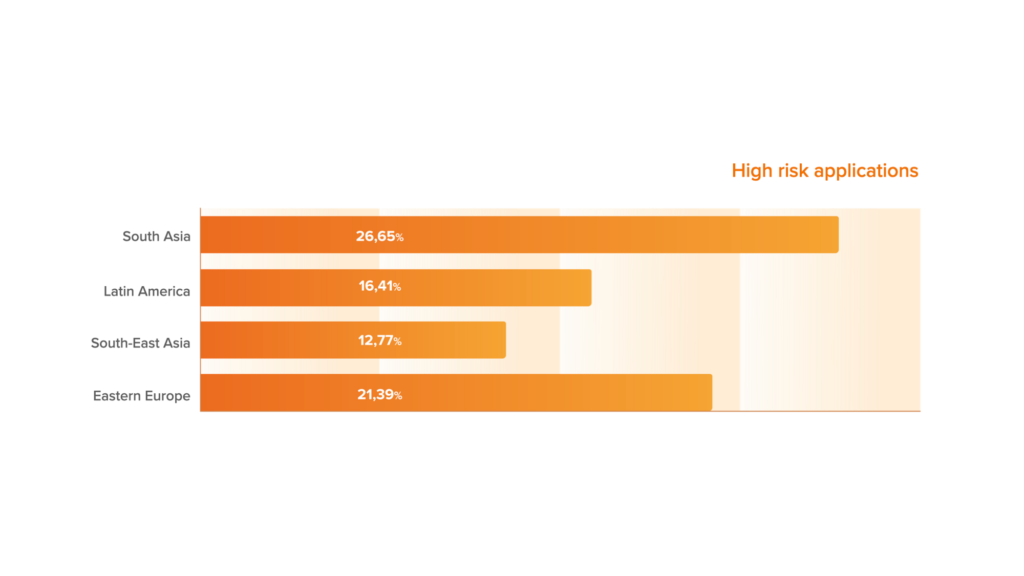
As you can see here, the level of high-risk applications in South Asia and Eastern Europe is the highest. Usually, such figures occur in countries with low income of the population and also may indicate the rise of credit shopping in the region.
The highest level of average inflow device quality has been spotted in the regions of South-East Asia and Eastern Europe. The lowest rate has been recorded in the countries of South Asia.
We are now penetrating Africa and before the end of the year 2023, we shall provide an in-depth analysis that will include Africa as a region.
Are fintechs prone to more external risks rather than internal ones?
Both external and internal risk are integral. At times is a combination of both internal and external risk factors. The balance is on information asymmetry where the lender/fintech has limited technology and alternative data especially if the applicant identification has been compromised by internal or external factors.
Why should CIOs and CXOs be more prepared when planning for the year?
Any risk officer or a person responsible for fraud prevention in a company should always remember that successful operation in the online business is based on three components: data, technology, and team.
The data includes various sources that are used to assess the risk of borrowers.
Technologies include methods for collecting and processing data, building various models, filters, and rules, as well as building online flow risk metrics based on previously collected data.
A team that includes risk officers, anti-fraud specialists, and other experts, who know how to use various analyzing tools and monitoring metrics, can quickly make changes to the decision-making system if some metrics go into the “red zone” in terms of risk level.
Since fintechs in Africa operate via mobile money infrastructure, how can the mobile infrastructure be made more secure?
- Use strong passwords/biometrics-Strong passwords coupled with biometric features, such as fingerprint authenticators, make unauthorized access nearly impossible. The mobile device to allows two-factor authentication. (reducing the approval level for applications, introducing additional methods of user verification, one time password-OTP etc.);
- An emergency button on the device to deactivate an applications or debit/credit card once the user realises that his/her devise has been compromised-For example a click of a button and his/her bank account Is deactivated immediately.
- Technology-Invest in technologies (Machine Learning) in order to detect the risk of fraud in real time – hundreds of fraudsters can attack the resource of a financial institution in a short period of time;
- Encrypt your device-The device to be bundled with a built-in encryption feature. Encryption is the process of making data unreadable. Decryption is converting the unreadable data into normal data. This is important in case of theft, and it prevents unauthorized access.
- Restrict the use of your users’ personal data. Please note: often personal data is not required for auxiliary and vendor tasks – it is often possible to find an alternative solution based on anonymized sessions or tokens;
- Pay special attention to the user’s behavior on your online resource in order to identify hidden correlations.
Follow us on Telegram, Twitter, and Facebook, or subscribe to our weekly newsletter to ensure you don’t miss out on any future updates. Send tips to info@techtrendske.co.ke.



